Τι είναι το Black Basta:
Το Black Basta είναι ένα ransomware που εμφανίστηκε τον Απρίλιο του 2022 που στοχευει κυρίως σε επιχειρήσεις . Έχει παρατηρηθεί ότι το ransomware προσθέτει την κατάληξη .basta στα αρχεία που έχουν κρυπτογραφηθεί. Οι συχνές επιθέσεις μόλυνσης του Black Basta είναι phishing, torrent websites, and adware. Το ransomware έχει δύο παραλλαγές που περιλαμβάνουν την παραλλαγή για Windows και την παραλλαγή για το VMWare ESXi. Η παραλλαγή του κακόβουλου λογισμικού για το περιβάλλον Windows στοχεύει συστήματα 32-bit και 64-bit των εκδόσεων Windows XP, Vista, 7, 10 και 11. Μετά την κρυπτογράφηση, η ταπετσαρία της μολυσμένης μηχανής αλλάζει, και ένα αρχείο readme.txt προστίθεται σε όλους τους φακέλους της μολυσμένης μηχανής. Το σημείωμα προειδοποιεί ότι εάν δεν πληρωθούν τα λύτρα, τα αρχεία θα διαρρεύσουν στην ιστοσελίδα Tor των κυβερνοεγκληματιών. Το μήνυμα περιέχει επίσης ένα σύνδεσμο προς την ιστοσελίδα Tor, όπου τα θύματα μπορούν να επικοινωνήσουν με τους επιτιθέμενους.
Παρακάτω παρουσιάζονται ορισμένες δραστηριότητες που δημιουργεί το Black Basta κατά την εκτέλεσή του:
Dropped .ico and .jpg Black Basta files: Κατά την εκτέλεση του Black Basta, παρατηρείται η λήψη των αρχείων dlaksjdoiwq.jpg και fkdjsadasd.ico στον φάκελο Appdata\Temp ενός μολυσμένου συστήματος.
Shadow copy deletion: Μετά την εκτέλεση, το κακόβουλο λογισμικό Black Basta χρησιμοποιεί ένα τερματικό και εκτελεί μια εντολή για τη διαγραφή των shadow copies σε ένα μολυσμένο σύστημα χρησιμοποιώντας το vssadmin.exe. Το shadow copies, γνωστό επίσης ως VSS ή Volume Snapshot Service, χρησιμοποιείται για τη δημιουργία αντιγράφων ασφαλείας ή στιγμιότυπων των αρχείων και των μονάδων αποθήκευσης.
Creation of readme.txt files: Παρατηρήσαμε επίσης ότι το κακόβουλο λογισμικό Black Basta δημιούργει ένα αρχείο readme.txt σε όλους τους καταλόγους του μολυσμένου υπολογιστή. Το αρχείο readme.txt περιέχει ένα μήνυμα Black Basta με το URL ενός ιστότοπου Tor, όπου τα θύματα μπορούν να αλληλεπιδρούν και να διαπραγματεύονται με τους επιτιθέμενους.
Defense evasion: Τέλος, το κακόβουλο λογισμικό απενεργοποιεί τους security monitoring agents στο μολυσμένο υπολογιστή.
Εντοπισμός του Black Basta:
Το Cyber Radar έχει δύο τεχνικές εντοπισμού του Black Basta τα εξής παρακάτω:
Καταγραφή και αξιολόγηση συμβάντων στα Windows: Το Cyber Radar έχει την δυνατότητα να εντοπίζει αυτές τις ενέργειες που αναφεραμε όταν γίνονται σε ένα σύστημα και οταν εντοπίζονται δημιουργείται η αντίστοιχη ειδοποίηση στο Dashboard. Οι ειδοποιησεις αναλύονται και αξιολογούνται και κατόπιν πραγματοποιούνται οι απαραίτητες ενέργειες για την αντιμετώπιση του συμβάντος.
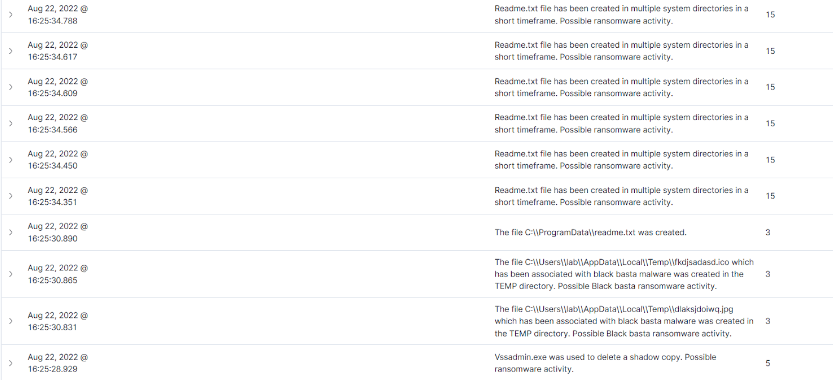
File Integrity Monitoring (FIM): Ανιχνεύει τα αρχεία όταν δημιουργούνται, διαγράφονται ή αλλάζουν και καταγράφει τα hash των αρχείων χρησιμοποιώντας SHA1, MD5, SHA256 και IMPHASH. Κατόπιν συγκρίνει τα hash όλων των αρχείων με τη βάση δεδομένων μας (Threat Intelligence) και αν κάποιο hash ταυτιστεί με αυτο του Pandora θα δημιουργηθεί η αντίστοιχη ειδοποίηση στο Dashboard του Cyber Radar και αμέσως θα διαγραφεί αυτόματα.
Μην αφήσετε την ασφάλεια της επιχείρησής σας στην τύχη.
Επικοινωνήστε μαζί μας σήμερα για να δείτε πώς το Cyber Radar μπορεί να προστατεύσει τα δεδομένα και τη φήμη της εταιρείας σας. Μια επένδυση στην ασφάλεια της επιχείρησής σας είναι μια επένδυση για το μέλλον της.
Ανακαλύψτε περισσότερα ή ζητήστε ένα DEMO από εδώ: https://www.audax.gr/gia-epixeiriseis/cyber-radar-unified-xdr-siem-platform/

