Lockbit 3.0 ransomware :
Lockbit is considered one of the most notorious and active ramsomware . Lockbit Ransomware uses a variety of techniques to target critical infrastructure and organizations around the world. Lockbit ransomware attacks primarily target Windows operating system devices, using multiple teachniques for initial access, including exploiting publicly accessible RDP (Remote Desktop Protocol) ports. It also exploits unpatchable server vulnerabilities that allow malicious users remote access to target networks. Translated with www.DeepL.com/Translator (free version)
The LockBit malware first appeared in September 2019 and during that time it has been updated twice to include new forms of infection and techniques to avoid detection. The latest version is Lockbit 3.0, which was released in June 2022.
The following are actions that Lockbit 3.0 ransomware does:
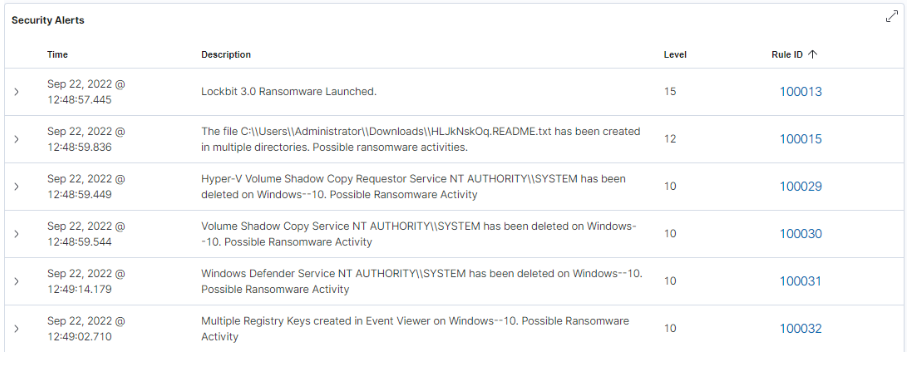
1) Uses a form of authentication ("special key" - access token) to decrypt the source code of the ransomware before it is executed on the victim's machine, for example: -k LocalServiceNetworkRestricted -pass db66023ab2abcbcb9957fb01ed50cdfa6a.
2) The ransomware leaves the ransom request in multiple folders and then encrypts all the files at the destination. The requests are usually in the format .README.txt. The extension of the encrypted files is changed to a random string. Examples of random strings used are HLJkNskOq and 19MqZqZ0s.
3) It continues by changing the icons of the encrypted files using the .ico file written in the C:\ProgramData\ folder by the malware.
4) Disables Windows Defender and Event Log services.
5) Disables and deletes the Volume Shadow Copy and Hyper-V Volume Shadow Copy Requestor services.
Locating the Lockbit:
Cyber Radar has two Lockbit detection techniques as follows:
File Integrity Monitoring (FIM): It detects files when they are created, deleted or changed and records the hash of the files using SHA1, MD5, SHA256 and IMPHASH. It then compares the hash of all files with our database (Threat Intelligence) and if any hash matches that of Pandora the corresponding alert will be generated in the Cyber Radar Dashboard and immediately deleted automatically.
Windows event logging and evaluation: Cyber Radar has the ability to detect these actions mentioned above when they occur on a system and when they are detected the corresponding alert is generated in the Dashboard. The alerts are analyzed and evaluated and then the necessary actions are taken to address the incident.