What is Venom Rat:
Venom RAT is a remote access tool that targets Windows operating systems and allows attackers to gain full access and remote control of victims' machines. It is usually distributed as a malicious attachment to spam emails, malicious advertising and other social engineering techniques. The main purpose of this RAT is to steal and extract information to a command and control server (C2 Server).
Venom RAT provides the following features:
- Extraction of data from browsers, browser cookies, credit card details, autofills and passwords.
- Collection of system information.
- Sending data from an infected system to a Control and Command Server (C2 Server).
- Keystroke logging on the infected system.
- Record video and audio using the system's camera and microphone.
Behavioral analysis:
When Venom RAT is run on a system, it performs the following behaviors:
- Venom RAT creates a copy of itself in the C:\Users\AppData\Roaming\ folder with the filename svchost.exe, pretending to be a legitimate file.
- Venom RAT creates a registry key in the path \SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ for the created svchost.exe file to ensure that it is executed each time the infected victim's system is rebooted.
- Venom RAT is injected into multiple .dll files.
- Venom RAT creates .tmp and .tmp.bat files in the folder C:\Users<USERNAME>\AppData\Local\Temp.
- Venom RAT executes the generated .tmp.bat file.
- Venom RAT uses cmd.exe to delete the created .tmp.bat file.
Locating the Venom Rat:
Cyber Radar has two Venom Rat detection techniques as follows:
Windows event logging and evaluation: Cyber Radar has the ability to detect these actions mentioned above when they occur on a system and when they are detected the corresponding alert is generated in the Dashboard. The alerts are analyzed and evaluated and then the necessary actions are taken to address the incident.
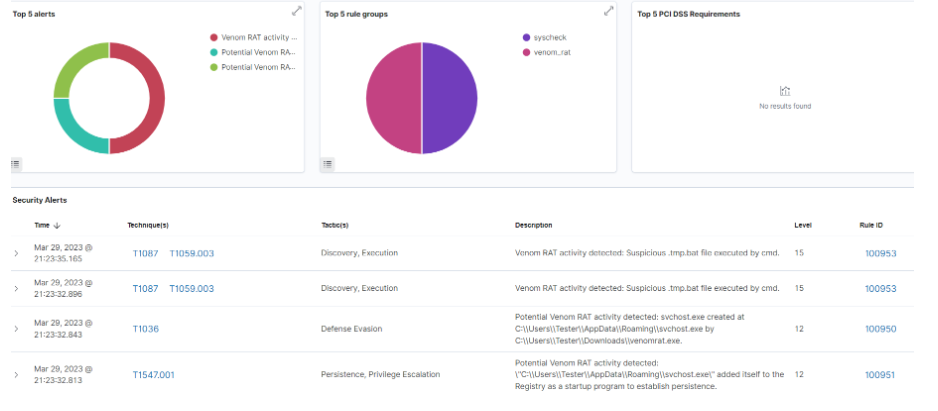
File Integrity Monitoring (FIM): It detects files when they are created, deleted or changed and records the hash of the files using SHA1, MD5, SHA256 and IMPHASH. It then compares the hash of all files with our database (Threat Intelligence) and if any hash matches that of Pandora the corresponding alert will be generated in the Cyber Radar Dashboard and immediately deleted automatically.
Μην αφήσετε την ασφάλεια της επιχείρησής σας στην τύχη.
Επικοινωνήστε μαζί μας σήμερα για να δείτε πώς το Cyber Radar μπορεί να προστατεύσει τα δεδομένα και τη φήμη της εταιρείας σας. Μια επένδυση στην ασφάλεια της επιχείρησής σας είναι μια επένδυση για το μέλλον της.
Ανακαλύψτε περισσότερα ή ζητήστε ένα DEMO από εδώ: https://www.audax.gr/gia-epixeiriseis/cyber-radar-unified-xdr-siem-platform/

