Αναβαθμίζουμε την ασφάλεια των πελατών μας!
Τι είναι το Vidar Infostealer :
Το Vidar infostealer είναι ένα κακόβουλο λογισμικό που κλέβει ευαίσθητες πληροφορίες από πορτοφόλια κρυπτονομισμάτων, web browsers και άλλες εφαρμογές όπως το WinSCP, το Telegram και το Authy 2FA σε μολυσμένα συστήματα Windows. Μπορεί να συλλέξει αποθηκευμένα διαπιστευτήρια, πληροφορίες σχετικά με το υικό και το λογισμικό στα μολυσμένα συστήματα. Το κακόβουλο λογισμικό αποστέλλει τα κλεμμένα δεδομένα σε έναν απομακρυσμένο διακομιστή ελέγχου και εντολών (C2).
Στο παρελθόν, το Vidar επικοινωνούσε με διακομιστές C2 που ήταν κωδικοποιημένοι μέσα στο κακόβουλο λογισμικό. Πρόσφατα, το κακόβουλο λογισμικό επικοινωνεί με διακομιστές C2 που αλλάζουν συνεχώς και τα λαμβάνει από νόμιμες ιστοσελίδες.
Οι κακόβουλοι χρήστες συνήθως διανέμουν το Vidar μέσω αποστολής ψεύτικων emails, cracked versions εμπορικών εφαρμογών και keygens. Πρόσφατα, οι κακόβουλοι χρήστες έχουν καταχραστεί το AnyDesk και το Notepad++(cracked versions) για να διανέμουν αυτό το κακόβουλο λογισμικό.
Ανάλυση συμπεριφοράς:
Όταν εκτελείται το Vidar infostealer σε ένα σύστημα, κάνει τις παρακάτω συμπεριφορές:
• Το Vidar κάνει λήψη των αρχείων freebl3.dll, mozglue.dll, msvcp140.dll, nss3.dll, softokn3.dll και vcruntime140.dll από έναν C2 διακομιστή και τα αποθηκεύει στον φάκελο C:\ProgramData του μολυσμένου συστήματος. Το Vidar χρησιμοποιεί αυτά τα αρχεία DLL για να κλέψει πληροφορίες από το μολυσμένο σύστημα.
• Το κακόβουλο λογισμικό δημιουργεί έναν φάκελο C:\ProgramData<ΤΥΧΑΙΟΣ_ΦΑΚΕΛΟΣ>\files . Αυτός ο φάκελος περιέχει υποφακέλους και αρχεία που αποθηκεύουν τα κλεμμένα δεδομένα από το μολυσμένο σύστημα.
• Το Vidar αρχειοθετεί τα κλεμμένα δεδομένα σε ένα αρχείο C:\ProgramData<ΤΥΧΑΙΟΣ_ΦΑΚΕΛΟΣ><ΜΗΧΑΝΗ_GUID>.zip και το αποστέλλει σε έναν διακομιστή C2.
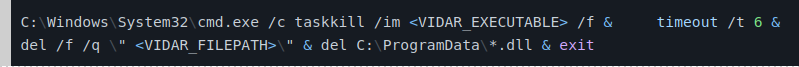
• Το κακόβουλο λογισμικό τελικά διαγράφει τον εαυτό του και τα αρχεία που δημιουργεί από το μολυσμένο σύστημα εκτελώντας την ακόλουθη εντολή:
Εντοπισμός του Vidar infostealer:
Το Cyber Radar έχει δύο τεχνικές εντοπισμού του Vidar infostealer τα εξής παρακάτω:
Καταγραφή και αξιολόγηση συμβάντων στα Windows: Το Cyber Radar έχει την δυνατότητα να εντοπίζει αυτές τις ενέργειες που αναφεραμε όταν γίνονται σε ένα σύστημα και οταν εντοπίζονται δημιουργείται η αντίστοιχη ειδοποίηση στο Dashboard. Οι ειδοποιησεις αναλύονται και αξιολογούνται και κατόπιν πραγματοποιούνται οι απαραίτητες ενέργειες για την αντιμετώπιση του συμβάντος.
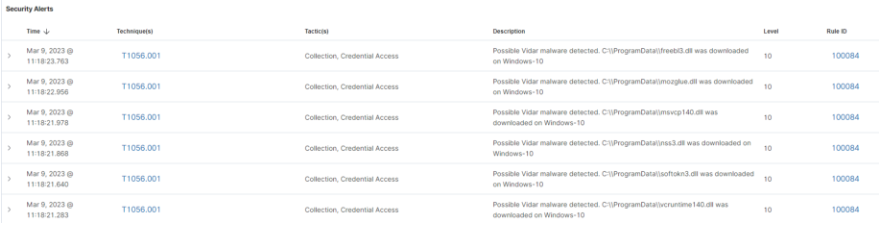
(Εικόνα 1 : Malicious DLL files downloaded)
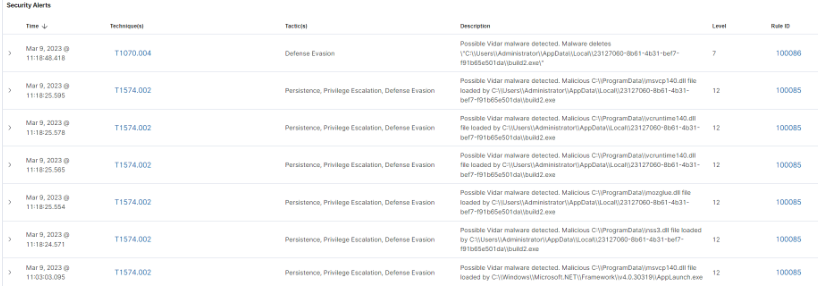
(Εικόνα 2: Malicious DLL files loaded by Vidar, and Vidar deleted a malicious process)
File Integrity Monitoring (FIM): Ανιχνεύει τα αρχεία όταν δημιουργούνται, διαγράφονται ή αλλάζουν και καταγράφει τα hash των αρχείων χρησιμοποιώντας SHA1, MD5, SHA256 και IMPHASH. Κατόπιν συγκρίνει τα hash όλων των αρχείων με τη βάση δεδομένων μας (Threat Intelligence) και αν κάποιο hash ταυτιστεί με αυτο του Pandora θα δημιουργηθεί η αντίστοιχη ειδοποίηση στο Dashboard του Cyber Radar και αμέσως θα διαγραφεί αυτόματα.
Μην αφήσετε την ασφάλεια της επιχείρησής σας στην τύχη.
Επικοινωνήστε μαζί μας σήμερα για να δείτε πώς το Cyber Radar μπορεί να προστατεύσει τα δεδομένα και τη φήμη της εταιρείας σας. Μια επένδυση στην ασφάλεια της επιχείρησής σας είναι μια επένδυση για το μέλλον της.
Ανακαλύψτε περισσότερα ή ζητήστε ένα DEMO από εδώ: https://www.audax.gr/gia-epixeiriseis/cyber-radar-unified-xdr-siem-platform/










